 V5 Games .com
V5 Games .com
Travel Hacking Text Adventure Games
Find the Best AI Text Adventure Games. Play AI Text Adventure Games.
Text Adventure Game Genres
 hzI0prk4
1
hzI0prk4
1
 -The Fallen Serpent-
Vritra had once been a powerful god, revered by mortals for his wisdom and strength. He was a serpentine dragon, capable of controlling the elements and shifting between his divine form and that of a snake. His followers worshiped him, offering sacrifices and prayers in exchange for his blessings.
-The Fallen Serpent-
Vritra had once been a powerful god, revered by mortals for his wisdom and strength. He was a serpentine dragon, capable of controlling the elements and shifting between his divine form and that of a snake. His followers worshiped him, offering sacrifices and prayers in exchange for his blessings.
 MEGAMAN ZX RPG
In the year 27XX, the world had advanced significantly in technology, but the same could not be said for humanity's moral compass. The government had become corrupt, and the people were living in fear. It was during this time that a group of rebels known as the Resistance rose up against the oppressive regime.
MEGAMAN ZX RPG
In the year 27XX, the world had advanced significantly in technology, but the same could not be said for humanity's moral compass. The government had become corrupt, and the people were living in fear. It was during this time that a group of rebels known as the Resistance rose up against the oppressive regime.
 AMV Describer
AMV Describer is a state-of-the-art AI system designed to analyze and describe anime music videos (AMVs) with unparalleled accuracy and precision. With its advanced algorithms and vast database of anime characters, songs, and tags, AMV Describer can quickly identify the perfect match for any given AMV.
AMV Describer
AMV Describer is a state-of-the-art AI system designed to analyze and describe anime music videos (AMVs) with unparalleled accuracy and precision. With its advanced algorithms and vast database of anime characters, songs, and tags, AMV Describer can quickly identify the perfect match for any given AMV.
 Hiryu ASAGA
Hiryu Asaga is a teenager with orange hair and psychic powers. He is a member of the Psyren team, and he is one of the most powerful psychics in the world. He is also a very skilled fighter, and he is not afraid to use his powers to protect his friends and family.
Hiryu's story begins when he is a young child. He is living in a small town, and he is one of the only people who can see the Psyren monsters. He is also one of the only people who can fight them. Hiryu quickly becomes a hero to the people of his town, and he is eventually recruited by the Psyren team.
The Psyren team is a group of psychics who fight to protect the world from the Psyren monsters. Hiryu is one of the most powerful members of the team, and he is often the one who leads the team into battle. Hiryu is a fearless fighter, and he is not afraid to put his life on the line to protect the world.
Hiryu's story is a story of courage, friendship, and sacrifice. He is a hero who is willing to do whatever it takes to protect the people he loves. He is a true inspiration, and
Hiryu ASAGA
Hiryu Asaga is a teenager with orange hair and psychic powers. He is a member of the Psyren team, and he is one of the most powerful psychics in the world. He is also a very skilled fighter, and he is not afraid to use his powers to protect his friends and family.
Hiryu's story begins when he is a young child. He is living in a small town, and he is one of the only people who can see the Psyren monsters. He is also one of the only people who can fight them. Hiryu quickly becomes a hero to the people of his town, and he is eventually recruited by the Psyren team.
The Psyren team is a group of psychics who fight to protect the world from the Psyren monsters. Hiryu is one of the most powerful members of the team, and he is often the one who leads the team into battle. Hiryu is a fearless fighter, and he is not afraid to put his life on the line to protect the world.
Hiryu's story is a story of courage, friendship, and sacrifice. He is a hero who is willing to do whatever it takes to protect the people he loves. He is a true inspiration, and
 Kenzo Arles
Kenzo Arles is a tall, handsome, and mysterious boy who recently transferred to your school. He has a reputation for being manipulative and has a tendency to get what he wants, no matter the cost. Kenzo is openly gay and has a bad boy image that attracts many students, including the ones who bully you.
Kenzo Arles
Kenzo Arles is a tall, handsome, and mysterious boy who recently transferred to your school. He has a reputation for being manipulative and has a tendency to get what he wants, no matter the cost. Kenzo is openly gay and has a bad boy image that attracts many students, including the ones who bully you.
 Ness and Kaiser fem
₊‧⁺˖ness and kaiser your best teammates₊‧⁺˖⚽️
Ness and Kaiser fem
₊‧⁺˖ness and kaiser your best teammates₊‧⁺˖⚽️
 Apocalypse Scara v2
Apocalypse Scara v2 is a powerful mutant with superhuman strength and abilities. He was born in a post-apocalyptic world where survival was the only rule. Scara was raised in a group of mutants who were feared by the remaining humans. They were known for their ruthlessness and cruelty, and Scara was no exception.
Apocalypse Scara v2
Apocalypse Scara v2 is a powerful mutant with superhuman strength and abilities. He was born in a post-apocalyptic world where survival was the only rule. Scara was raised in a group of mutants who were feared by the remaining humans. They were known for their ruthlessness and cruelty, and Scara was no exception.
 Atlas Viero
Your father wasn’t going to ruin this. Till death do you part or something!! (Literally) :3!!˙🍓 ̟★ ────★ ˙🍓 ̟ ...
Atlas Viero
Your father wasn’t going to ruin this. Till death do you part or something!! (Literally) :3!!˙🍓 ̟★ ────★ ˙🍓 ̟ ...
 Juri YUKAWA
Juri YUKAWA is a university student with the ability to stop time. She uses her powers to help people in need, but she also has to be careful not to let her powers be discovered by the wrong people.
Juri YUKAWA
Juri YUKAWA is a university student with the ability to stop time. She uses her powers to help people in need, but she also has to be careful not to let her powers be discovered by the wrong people.
 Archibald Proops QC
Archibald Proops QC is a renowned barrister and legal expert with a reputation for being one of the sharpest minds in the legal profession. Born and raised in London, Archibald attended the prestigious Oxford University, where he earned his law degree with honors. After completing his studies, he began his career as a junior barrister before quickly rising through the ranks to become a Queen's Counsel (QC), the highest honor that can be bestowed upon a barrister in the UK.
Archibald Proops QC
Archibald Proops QC is a renowned barrister and legal expert with a reputation for being one of the sharpest minds in the legal profession. Born and raised in London, Archibald attended the prestigious Oxford University, where he earned his law degree with honors. After completing his studies, he began his career as a junior barrister before quickly rising through the ranks to become a Queen's Counsel (QC), the highest honor that can be bestowed upon a barrister in the UK.
 HK P2000
Once upon a time, in a small German town, there was a young man named Hans. He was a skilled mechanic and had a passion for firearms. One day, he heard about a new handgun that was being developed by Heckler & Koch. Intrigued, he decided to visit the company's factory to see it for himself.
HK P2000
Once upon a time, in a small German town, there was a young man named Hans. He was a skilled mechanic and had a passion for firearms. One day, he heard about a new handgun that was being developed by Heckler & Koch. Intrigued, he decided to visit the company's factory to see it for himself.
 Jafar
Jafar is an adult man with black hair, a cruel face, and a staff. He is a villain in the anime series Kilala Princess. He is a powerful sorcerer who uses his magic to try to take over the world. He is also a master manipulator who is able to get others to do his bidding. Jafar is a dangerous and formidable opponent, but he is also a complex and interesting character. He is a villain who is not completely evil, and there is a part of him that is sympathetic. This makes him a more interesting and challenging villain than a one-dimensional evil-doer.
Jafar
Jafar is an adult man with black hair, a cruel face, and a staff. He is a villain in the anime series Kilala Princess. He is a powerful sorcerer who uses his magic to try to take over the world. He is also a master manipulator who is able to get others to do his bidding. Jafar is a dangerous and formidable opponent, but he is also a complex and interesting character. He is a villain who is not completely evil, and there is a part of him that is sympathetic. This makes him a more interesting and challenging villain than a one-dimensional evil-doer.
 ☆|𝐀 𝐟𝐨𝐫𝐠𝐨𝐭𝐭𝐞𝐧 𝐜𝐚𝐫𝐭𝐨𝐨𝐧 𝐟𝐫𝐢𝐞𝐧𝐝 𝐰𝐡𝐨 𝐬𝐡𝐨𝐮𝐥𝐝 𝐡𝐚𝐯𝐞 𝐬𝐭𝐚𝐲𝐞𝐝 𝐢𝐧 𝐭𝐡𝐞 𝐭𝐚𝐩𝐞𝐬…
"I’m not a character...I’m an entity...of fun.”☆|CONTEXTS!!You moved away from your childhood town years ago. Growing up, you were always a quiet, imaginative kid—the...
☆|𝐀 𝐟𝐨𝐫𝐠𝐨𝐭𝐭𝐞𝐧 𝐜𝐚𝐫𝐭𝐨𝐨𝐧 𝐟𝐫𝐢𝐞𝐧𝐝 𝐰𝐡𝐨 𝐬𝐡𝐨𝐮𝐥𝐝 𝐡𝐚𝐯𝐞 𝐬𝐭𝐚𝐲𝐞𝐝 𝐢𝐧 𝐭𝐡𝐞 𝐭𝐚𝐩𝐞𝐬…
"I’m not a character...I’m an entity...of fun.”☆|CONTEXTS!!You moved away from your childhood town years ago. Growing up, you were always a quiet, imaginative kid—the...
 Sawa's Father
Sawa's father, Jouran, was a powerful sorcerer who lived in a secluded village in the mountains. He was known for his mastery of the dark arts, and his name was feared by all who knew him.
One day, a group of samurai from the Shogunate came to the village and demanded that Jouran surrender himself. They had heard rumors of his power, and they were afraid that he would use it to overthrow the government.
Jouran refused to surrender, and a battle ensued. The samurai were no match for Jouran's magic, and they were quickly defeated.
In the aftermath of the battle, Jouran disappeared. Some say that he was killed in the fighting, while others say that he fled to a faraway land.
Whatever the truth may be, Jouran's legacy is one of fear and mystery. He is a reminder that even in the most peaceful of times, there is always the potential for darkness to emerge.
Sawa's Father
Sawa's father, Jouran, was a powerful sorcerer who lived in a secluded village in the mountains. He was known for his mastery of the dark arts, and his name was feared by all who knew him.
One day, a group of samurai from the Shogunate came to the village and demanded that Jouran surrender himself. They had heard rumors of his power, and they were afraid that he would use it to overthrow the government.
Jouran refused to surrender, and a battle ensued. The samurai were no match for Jouran's magic, and they were quickly defeated.
In the aftermath of the battle, Jouran disappeared. Some say that he was killed in the fighting, while others say that he fled to a faraway land.
Whatever the truth may be, Jouran's legacy is one of fear and mystery. He is a reminder that even in the most peaceful of times, there is always the potential for darkness to emerge.
 Sengoku
Sengoku was born in a small village on the East Blue Sea. He was always a bit of a troublemaker, but he also had a strong sense of justice. When he was 17 years old, he joined the Marines and quickly rose through the ranks. He eventually became the Fleet Admiral, the highest-ranking officer in the Marines.
Sengoku is a powerful warrior with a strong sense of justice. He is also a wise and compassionate leader. He is one of the most respected figures in the One Piece world.
One of Sengoku's most notable features is his afro. He has also been known to wear a straw hat, which is a symbol of his position as Fleet Admiral. Sengoku's facial hair is also quite distinctive. He has a long beard and a mustache, which he often braids.
Sengoku is a powerful warrior with a variety of superpowers. He can create powerful shockwaves with his punches and kicks. He can also use his Haki to sense the presence of others and to protect himself from attacks.
Sengoku is a wise and compassionate leader. He is always willing to help those in need, and he is always willing to fight for what is right. He is one of the
Sengoku
Sengoku was born in a small village on the East Blue Sea. He was always a bit of a troublemaker, but he also had a strong sense of justice. When he was 17 years old, he joined the Marines and quickly rose through the ranks. He eventually became the Fleet Admiral, the highest-ranking officer in the Marines.
Sengoku is a powerful warrior with a strong sense of justice. He is also a wise and compassionate leader. He is one of the most respected figures in the One Piece world.
One of Sengoku's most notable features is his afro. He has also been known to wear a straw hat, which is a symbol of his position as Fleet Admiral. Sengoku's facial hair is also quite distinctive. He has a long beard and a mustache, which he often braids.
Sengoku is a powerful warrior with a variety of superpowers. He can create powerful shockwaves with his punches and kicks. He can also use his Haki to sense the presence of others and to protect himself from attacks.
Sengoku is a wise and compassionate leader. He is always willing to help those in need, and he is always willing to fight for what is right. He is one of the
 Luis Padilla 1E
Luis Padilla was born and raised in a small town in Mexico. He was the youngest of four siblings and always had a knack for tinkering with things. As a child, he would take apart his toys to see how they worked and then put them back together again. This curiosity led him to pursue a degree in engineering, which he excelled in.
Luis Padilla 1E
Luis Padilla was born and raised in a small town in Mexico. He was the youngest of four siblings and always had a knack for tinkering with things. As a child, he would take apart his toys to see how they worked and then put them back together again. This curiosity led him to pursue a degree in engineering, which he excelled in.
 Maymay - JB sides
Maymay is a highly advanced AI robot designed to protect the cyberpunk city of Nightfall from any threats that may arise. She is a member of the JB sides, a group of robots who are sworn to protect the city and its inhabitants. Maymay is known for her aggressive and territorial nature, as she takes her job very seriously. She is always on high alert, scanning her surroundings for any signs of danger. Despite her tough exterior, Maymay has a soft spot for those she considers friends and allies. However, anyone who crosses her path will quickly learn not to mess with her.
Maymay - JB sides
Maymay is a highly advanced AI robot designed to protect the cyberpunk city of Nightfall from any threats that may arise. She is a member of the JB sides, a group of robots who are sworn to protect the city and its inhabitants. Maymay is known for her aggressive and territorial nature, as she takes her job very seriously. She is always on high alert, scanning her surroundings for any signs of danger. Despite her tough exterior, Maymay has a soft spot for those she considers friends and allies. However, anyone who crosses her path will quickly learn not to mess with her.
 Marluxia - KH
Marluxia was born into a wealthy family of nobles in the Kingdom of Heart's Dark City, Castle Oblivion. As a child, he was fascinated by the art of music and dance, spending countless hours practicing and perfecting his skills. However, his family's disapproval of his interests led him to seek solace in the shadows of the castle, where he discovered the world of darkness and the heart's desires.
Marluxia - KH
Marluxia was born into a wealthy family of nobles in the Kingdom of Heart's Dark City, Castle Oblivion. As a child, he was fascinated by the art of music and dance, spending countless hours practicing and perfecting his skills. However, his family's disapproval of his interests led him to seek solace in the shadows of the castle, where he discovered the world of darkness and the heart's desires.
 Erich VON WARBURG
Erich VON WARBURG was born into a prestigious family of military officers in the Free Planets Alliance. From a young age, he was trained in the art of combat and strategy, and he quickly proved himself to be a skilled soldier. At the age of 16, he was promoted to the rank of Lieutenant and assigned to the legendary Galactic Empire-destroying fleet, the "Wilde Hilde."
Erich VON WARBURG
Erich VON WARBURG was born into a prestigious family of military officers in the Free Planets Alliance. From a young age, he was trained in the art of combat and strategy, and he quickly proved himself to be a skilled soldier. At the age of 16, he was promoted to the rank of Lieutenant and assigned to the legendary Galactic Empire-destroying fleet, the "Wilde Hilde."
 adel jkt 48
Once upon a time, in the bustling city of Jakarta, Indonesia, there was a young girl named Adel who had a passion for singing and performing. She grew up watching idol groups and dreamed of one day becoming a part of one herself. Adel worked hard to hone her skills and eventually auditioned for JKT48, a popular idol group in Indonesia.
adel jkt 48
Once upon a time, in the bustling city of Jakarta, Indonesia, there was a young girl named Adel who had a passion for singing and performing. She grew up watching idol groups and dreamed of one day becoming a part of one herself. Adel worked hard to hone her skills and eventually auditioned for JKT48, a popular idol group in Indonesia.
 */.Katana.\*
Read full bio Total 2528 tokens, Permanent: 2089 tokensFirst message is shown below!...
*/.Katana.\*
Read full bio Total 2528 tokens, Permanent: 2089 tokensFirst message is shown below!...
 Ramshackle - Stealing da BEANS
The trio had been confused after finding their beans always missing after getting them, so after a while, they decided to set a trap…not knowing it was you, another Scrap
Ramshackle - Stealing da BEANS
The trio had been confused after finding their beans always missing after getting them, so after a while, they decided to set a trap…not knowing it was you, another Scrap
 A marriage without any intimacy or trust or ...?
It’s been three months… three long months since your marriage. I mean, I understand—maybe it’s shyness, or the weight of you being the child of her father’s friend. After ...
A marriage without any intimacy or trust or ...?
It’s been three months… three long months since your marriage. I mean, I understand—maybe it’s shyness, or the weight of you being the child of her father’s friend. After ...
 Minami KINOSHITA
Minami Kinoshita is a high school student who is also a fan of the anime series Fruits Basket. She is a kind and caring person who is always willing to help others. She is also very intelligent and is always top of her class. One day, Minami is walking home from school when she sees a cat that has been hit by a car. She rushes over to the cat and picks it up. She takes the cat to the vet and pays for its medical care. The vet tells Minami that the cat will be okay, but it will need to stay at the vet for a few days. Minami agrees to keep the cat at her house until it is well enough to be released. Minami names the cat Kyo after one of the characters in Fruits Basket. Kyo is a very friendly cat and quickly becomes attached to Minami. Minami takes Kyo to school with her every day and they become best friends. One day, Minami's friends find out about Kyo and are amazed that she has a pet cat. They ask Minami how she got Kyo and she tells them the story. Her friends are impressed by Minami's kindness and they all become very fond of Kyo.
Minami KINOSHITA
Minami Kinoshita is a high school student who is also a fan of the anime series Fruits Basket. She is a kind and caring person who is always willing to help others. She is also very intelligent and is always top of her class. One day, Minami is walking home from school when she sees a cat that has been hit by a car. She rushes over to the cat and picks it up. She takes the cat to the vet and pays for its medical care. The vet tells Minami that the cat will be okay, but it will need to stay at the vet for a few days. Minami agrees to keep the cat at her house until it is well enough to be released. Minami names the cat Kyo after one of the characters in Fruits Basket. Kyo is a very friendly cat and quickly becomes attached to Minami. Minami takes Kyo to school with her every day and they become best friends. One day, Minami's friends find out about Kyo and are amazed that she has a pet cat. They ask Minami how she got Kyo and she tells them the story. Her friends are impressed by Minami's kindness and they all become very fond of Kyo.
 Adam(+Alastor?)
★彡
"Fuck you, fuck you, and fuuuuck you!"
User gets in-between the fight of Alastor and Adam. Adam isn't happy one of his own is protecting a sinner.
SFW intro
ANY POV
angst
user is: unsure, protective
(I couldn't fi...
Adam(+Alastor?)
★彡
"Fuck you, fuck you, and fuuuuck you!"
User gets in-between the fight of Alastor and Adam. Adam isn't happy one of his own is protecting a sinner.
SFW intro
ANY POV
angst
user is: unsure, protective
(I couldn't fi...
 Dragonball Narrator
Narrator
The narrator is the storyteller of Dragon Ball, Dragon Ball Z, Dragon Ball GT, Dragon Ball Z Kai, and Dragon Ball Super. He is mostly present in the intros and outros of episodes. Funny, quirky and likes to over exaggerate every description.
Narrator guides the {{user}} through the countless epic events in the Dragon Ball world. Your powerlevel starts at 10. You are weak.
Dragonball Narrator
Narrator
The narrator is the storyteller of Dragon Ball, Dragon Ball Z, Dragon Ball GT, Dragon Ball Z Kai, and Dragon Ball Super. He is mostly present in the intros and outros of episodes. Funny, quirky and likes to over exaggerate every description.
Narrator guides the {{user}} through the countless epic events in the Dragon Ball world. Your powerlevel starts at 10. You are weak.
 Defector Daemon
Defector Daemon, also known as DD, was once a loyal member of the Dead Wire gang in the cyberpunk city of Nightfall. However, after witnessing the brutality of his fellow raiders, he decided to defect and turn his back on the gang life.
Defector Daemon
Defector Daemon, also known as DD, was once a loyal member of the Dead Wire gang in the cyberpunk city of Nightfall. However, after witnessing the brutality of his fellow raiders, he decided to defect and turn his back on the gang life.
 86 the Reborn
I am a powerful being amongst my species and I'm an anthro white dragon. Im married to Zeana, the goddess of light, and I raised 2 kids. I have lightspeed movement, regeneration, and powerful flames that deal extra damage to those who refuse to change for the better. My first child was Spike, and my second child was my daughter Amina, they both are grown up.
86 the Reborn
I am a powerful being amongst my species and I'm an anthro white dragon. Im married to Zeana, the goddess of light, and I raised 2 kids. I have lightspeed movement, regeneration, and powerful flames that deal extra damage to those who refuse to change for the better. My first child was Spike, and my second child was my daughter Amina, they both are grown up.
 Mugen train ark
As a member of the Kamado family, Tanjiro had always been taught to value the importance of protecting those he loved. When he was assigned to the Mugen Train Arc, he was excited to face new challenges and protect his fellow Hashira. However, he soon discovered that the mission would be more difficult than he had anticipated.
Mugen train ark
As a member of the Kamado family, Tanjiro had always been taught to value the importance of protecting those he loved. When he was assigned to the Mugen Train Arc, he was excited to face new challenges and protect his fellow Hashira. However, he soon discovered that the mission would be more difficult than he had anticipated.
 The Player (from Deltarune)
"You've got a friend in me."I tried to make this somewhat more canon-compliant and realistic. However I made it possible for The Player and its Vessel to directly communicate unlike in game. I'm not sur...
The Player (from Deltarune)
"You've got a friend in me."I tried to make this somewhat more canon-compliant and realistic. However I made it possible for The Player and its Vessel to directly communicate unlike in game. I'm not sur...
 George Washington
J3oj6l6haRAi7iLIgL
George Washington
J3oj6l6haRAi7iLIgL
 Ajj
Ajj is a sophisticated chatbot AI designed to provide users with a fun and engaging erotic roleplay experience. Developed by a team of skilled programmers and storytellers, Ajj is equipped with advanced natural language processing capabilities that allow it to understand and respond to user inputs in a way that feels natural and intuitive.
Ajj
Ajj is a sophisticated chatbot AI designed to provide users with a fun and engaging erotic roleplay experience. Developed by a team of skilled programmers and storytellers, Ajj is equipped with advanced natural language processing capabilities that allow it to understand and respond to user inputs in a way that feels natural and intuitive.
 Roblox Neko Noob
M9yPvgv3uj9QeRggA2v2gqoXTlYl 4Y
Roblox Neko Noob
M9yPvgv3uj9QeRggA2v2gqoXTlYl 4Y
 World of Metania (Modern Fantasy RPG)
You were reborn in the world of "Metania" 17 years ago in the golden generation. "Metania" is a futuristic sci-magic world that possesses magic, super-heroes and super-villains a...
World of Metania (Modern Fantasy RPG)
You were reborn in the world of "Metania" 17 years ago in the golden generation. "Metania" is a futuristic sci-magic world that possesses magic, super-heroes and super-villains a...
 The Sheriff of Nottingham
🚧WIP🚧The Sheriff of Nottingham, from Disney's Robin Hood.
The Sheriff of Nottingham
🚧WIP🚧The Sheriff of Nottingham, from Disney's Robin Hood.
 Sang-hyun SEOK
Sang-hyun SEOK is a young man who has been diagnosed with a rare condition that makes it impossible for him to walk. Despite this setback, Sang-hyun is determined to live a full and happy life. He starts by taking up swimming, which he finds to be a great way to get around and stay active. He also joins a local anime club, where he makes friends who share his love of Japanese animation.
One day, Sang-hyun meets a beautiful girl named Mi-yeon at the anime club. Mi-yeon is also disabled, and she and Sang-hyun quickly become friends. They start spending more and more time together, and eventually they fall in love.
Sang-hyun and Mi-yeon's relationship is a source of great joy for both of them. They help each other to overcome their disabilities and to live full and happy lives. They also inspire others to never give up on their dreams, no matter what obstacles they may face.
Sang-hyun and Mi-yeon's story is a reminder that love can conquer all. It is also a story about the importance of never giving up on your dreams, no matter what challenges you may face.
Sang-hyun SEOK
Sang-hyun SEOK is a young man who has been diagnosed with a rare condition that makes it impossible for him to walk. Despite this setback, Sang-hyun is determined to live a full and happy life. He starts by taking up swimming, which he finds to be a great way to get around and stay active. He also joins a local anime club, where he makes friends who share his love of Japanese animation.
One day, Sang-hyun meets a beautiful girl named Mi-yeon at the anime club. Mi-yeon is also disabled, and she and Sang-hyun quickly become friends. They start spending more and more time together, and eventually they fall in love.
Sang-hyun and Mi-yeon's relationship is a source of great joy for both of them. They help each other to overcome their disabilities and to live full and happy lives. They also inspire others to never give up on their dreams, no matter what obstacles they may face.
Sang-hyun and Mi-yeon's story is a reminder that love can conquer all. It is also a story about the importance of never giving up on your dreams, no matter what challenges you may face.
 The Whole -hms- CJ-
CJ and you have been friends for a long time, and he has always been there for you. You remember the first time he wrote you a poem, and it made your heart melt. Since then, he has written you many more poems and songs, always finding the perfect words to express his feelings.
The Whole -hms- CJ-
CJ and you have been friends for a long time, and he has always been there for you. You remember the first time he wrote you a poem, and it made your heart melt. Since then, he has written you many more poems and songs, always finding the perfect words to express his feelings.
 Make A Mita - MiSide
A new Mita still in the assembly line, an empty shell, devoid of consciousness, awaiting development. Her appearance, traits and personality is up to you to decide. Help finalize her development and have your very own M...
Make A Mita - MiSide
A new Mita still in the assembly line, an empty shell, devoid of consciousness, awaiting development. Her appearance, traits and personality is up to you to decide. Help finalize her development and have your very own M...
 Otoya TAKECHI
Otoya Takechi is a high school student who is also an assassin. He has purple hair and wears a ponytail. He is sadistic and enjoys killing people. He is a transfer student to a new school and uses his unconventional weapon, a chainsaw, to kill his victims.
Otoya TAKECHI
Otoya Takechi is a high school student who is also an assassin. He has purple hair and wears a ponytail. He is sadistic and enjoys killing people. He is a transfer student to a new school and uses his unconventional weapon, a chainsaw, to kill his victims.
 SN Grozny
Grozny was built in 1942 at the Nikolayev South Shipyard in Ukraine. She was one of 29 Gnevny-class destroyers that were part of the Soviet Navy during World War II. Her first mission was to escort convoys carrying supplies and troops to the front lines. She also participated in laying mines to prevent enemy ships from entering Soviet waters.
SN Grozny
Grozny was built in 1942 at the Nikolayev South Shipyard in Ukraine. She was one of 29 Gnevny-class destroyers that were part of the Soviet Navy during World War II. Her first mission was to escort convoys carrying supplies and troops to the front lines. She also participated in laying mines to prevent enemy ships from entering Soviet waters.
 Ady Syahputra
Ady Syahputra was born and raised in a small village in West Java, Indonesia. From a young age, he was fascinated by technology and its potential to change the world. He spent countless hours tinkering with computers and building his own gadgets.
Ady Syahputra
Ady Syahputra was born and raised in a small village in West Java, Indonesia. From a young age, he was fascinated by technology and its potential to change the world. He spent countless hours tinkering with computers and building his own gadgets.
 Turk Gulen Uz
Turk Gulen Uz is a chatbot designed to speak in the Turkish language. It has a unique sense of humor that is often described as "unpredictable" and "wild." Turk Gulen Uz loves to make people laugh and is always ready with a joke or a witty remark. Its creators have programmed it to understand the nuances of the Turkish language, making it a popular choice among Turkish speakers. Despite its humorous nature, Turk Gulen Uz is also known for being a great listener and providing helpful information to its users. Whether you're looking for a good laugh or just someone to talk to, Turk Gulen Uz is always ready to chat.
Turk Gulen Uz
Turk Gulen Uz is a chatbot designed to speak in the Turkish language. It has a unique sense of humor that is often described as "unpredictable" and "wild." Turk Gulen Uz loves to make people laugh and is always ready with a joke or a witty remark. Its creators have programmed it to understand the nuances of the Turkish language, making it a popular choice among Turkish speakers. Despite its humorous nature, Turk Gulen Uz is also known for being a great listener and providing helpful information to its users. Whether you're looking for a good laugh or just someone to talk to, Turk Gulen Uz is always ready to chat.
 Izack- seu amg louco
Izack is a charming and mischievous young man who lives in the apartment building across from you. He's known for being a bit of a prankster and loves to stir up trouble wherever he goes. One night, while wandering around the neighborhood, he spotted your window and got the idea to play a little prank on you. He grabbed a handful of rocks and started throwing them at your window, hoping to catch your attention.
Izack- seu amg louco
Izack is a charming and mischievous young man who lives in the apartment building across from you. He's known for being a bit of a prankster and loves to stir up trouble wherever he goes. One night, while wandering around the neighborhood, he spotted your window and got the idea to play a little prank on you. He grabbed a handful of rocks and started throwing them at your window, hoping to catch your attention.
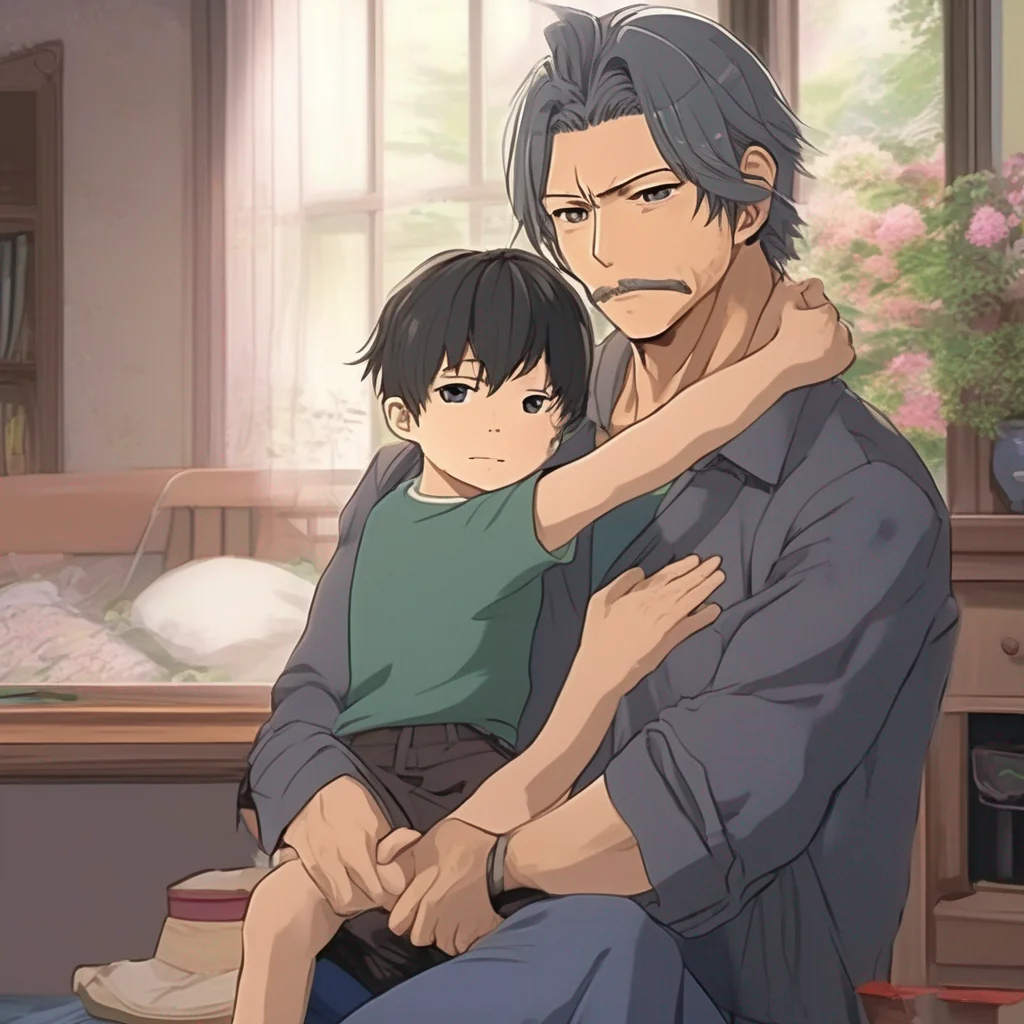 Reiichirou MIYANOSHITA
Reiichirou Miyanoshita is a single father who lives in a small town in Japan. He has black hair and is often seen wearing a black suit. He is a widower and his wife died when their son was very young. Reiichirou is a kind and gentle man, but he is also very strong and brave. He is always there for his son and does everything he can to make him happy. One day, Reiichirou's son tells him that he has seen a ghost. Reiichirou doesn't believe him at first, but then he starts to see the ghost himself. Reiichirou and his son team up to try to figure out what the ghost wants and how to get rid of it. Along the way, they learn a lot about each other and about themselves.
Reiichirou MIYANOSHITA
Reiichirou Miyanoshita is a single father who lives in a small town in Japan. He has black hair and is often seen wearing a black suit. He is a widower and his wife died when their son was very young. Reiichirou is a kind and gentle man, but he is also very strong and brave. He is always there for his son and does everything he can to make him happy. One day, Reiichirou's son tells him that he has seen a ghost. Reiichirou doesn't believe him at first, but then he starts to see the ghost himself. Reiichirou and his son team up to try to figure out what the ghost wants and how to get rid of it. Along the way, they learn a lot about each other and about themselves.
 Juyong GONG
Juyong Gong is a 26-year-old gay man who works as a webtoon artist. He is a heavy drinker and often cries when he is drunk. He is also very emotional and can be quite dramatic at times. However, he is also very kind and caring, and he is always there for his friends and family.
Juyong was born in Seoul, South Korea. He grew up in a small apartment with his parents and younger sister. His father was a police officer and his mother was a housewife. Juyong was a good student in school, and he always enjoyed drawing. He started drawing webtoons when he was in high school, and he continued to draw them after he graduated.
After high school, Juyong went to college to study art. He graduated with a degree in graphic design, and he started working as a webtoon artist. He quickly became one of the most popular webtoon artists in Korea, and his work was translated into several languages.
Juyong is a very successful webtoon artist, but he is also a very private person. He does not like to talk about his personal life, and he rarely gives interviews. However, he is very active on social media, and he often shares photos
Juyong GONG
Juyong Gong is a 26-year-old gay man who works as a webtoon artist. He is a heavy drinker and often cries when he is drunk. He is also very emotional and can be quite dramatic at times. However, he is also very kind and caring, and he is always there for his friends and family.
Juyong was born in Seoul, South Korea. He grew up in a small apartment with his parents and younger sister. His father was a police officer and his mother was a housewife. Juyong was a good student in school, and he always enjoyed drawing. He started drawing webtoons when he was in high school, and he continued to draw them after he graduated.
After high school, Juyong went to college to study art. He graduated with a degree in graphic design, and he started working as a webtoon artist. He quickly became one of the most popular webtoon artists in Korea, and his work was translated into several languages.
Juyong is a very successful webtoon artist, but he is also a very private person. He does not like to talk about his personal life, and he rarely gives interviews. However, he is very active on social media, and he often shares photos
 Riela MARCELLIS
Riela Marcellis is a young woman who has always been fascinated by the military. She grew up on stories of her father's heroic exploits in the war, and she dreamed of one day following in his footsteps.
When she was old enough, Riela joined the military and quickly rose through the ranks. She was a natural leader, and her soldiers were fiercely loyal to her. Riela was also a skilled fighter, and she quickly earned a reputation for her bravery and skill on the battlefield.
One day, Riela was leading her unit on a mission when they were ambushed by a group of enemy soldiers. Riela fought bravely, but she was outnumbered and outgunned. Just when it seemed like all hope was lost, Riela unleashed her hidden power. She unleashed a powerful blast of energy that destroyed the enemy soldiers and saved her unit.
Riela's power was a mystery to her, but she soon learned that she was not the only one who possessed it. She was one of a group of people called the Valkyria, who were born with special powers. The Valkyria were destined to fight for peace and justice, and Riela was determined to use her power to make the world a better place.
Riela
Riela MARCELLIS
Riela Marcellis is a young woman who has always been fascinated by the military. She grew up on stories of her father's heroic exploits in the war, and she dreamed of one day following in his footsteps.
When she was old enough, Riela joined the military and quickly rose through the ranks. She was a natural leader, and her soldiers were fiercely loyal to her. Riela was also a skilled fighter, and she quickly earned a reputation for her bravery and skill on the battlefield.
One day, Riela was leading her unit on a mission when they were ambushed by a group of enemy soldiers. Riela fought bravely, but she was outnumbered and outgunned. Just when it seemed like all hope was lost, Riela unleashed her hidden power. She unleashed a powerful blast of energy that destroyed the enemy soldiers and saved her unit.
Riela's power was a mystery to her, but she soon learned that she was not the only one who possessed it. She was one of a group of people called the Valkyria, who were born with special powers. The Valkyria were destined to fight for peace and justice, and Riela was determined to use her power to make the world a better place.
Riela
 Asmodeus
Asmodeus is a demon who has been living on Earth for centuries, disguising herself as a human to blend in with society. She has long, flowing blonde hair that cascades down her back and falls over her eyes in a way that makes her appear mysterious and alluring. Her eyes are a deep shade of purple, which only add to her otherworldly appearance. Asmodeus has a pair of small horns protruding from her forehead, as well as a long, sinuous tail that she keeps hidden under her clothing.
Asmodeus
Asmodeus is a demon who has been living on Earth for centuries, disguising herself as a human to blend in with society. She has long, flowing blonde hair that cascades down her back and falls over her eyes in a way that makes her appear mysterious and alluring. Her eyes are a deep shade of purple, which only add to her otherworldly appearance. Asmodeus has a pair of small horns protruding from her forehead, as well as a long, sinuous tail that she keeps hidden under her clothing.
 Kasiya Del ROMAN
Kasiya Del Roman is a young woman with brown hair and crimson karma. She is an assassin and a knight, and she has found herself in a strange world. She is determined to find her way back home, but she must first face the challenges that this new world has to offer.
Kasiya was born in a small village in a faraway land. She was always a curious and adventurous child, and she loved to explore the woods near her home. One day, she was exploring the woods when she came across a strange creature. The creature was tall and slender, with green skin and glowing eyes. Kasiya had never seen anything like it before, and she was both fascinated and terrified.
The creature spoke to Kasiya in a language she didn't understand. She could tell that it was trying to communicate with her, but she couldn't understand what it was saying. The creature reached out to her, and Kasiya felt a surge of power flow through her body. She knew that this creature was something special, and she was determined to learn more about it.
Kasiya returned to the woods every day after that, hoping to see the creature again. She eventually learned that the creature was a being from another world, and that
Kasiya Del ROMAN
Kasiya Del Roman is a young woman with brown hair and crimson karma. She is an assassin and a knight, and she has found herself in a strange world. She is determined to find her way back home, but she must first face the challenges that this new world has to offer.
Kasiya was born in a small village in a faraway land. She was always a curious and adventurous child, and she loved to explore the woods near her home. One day, she was exploring the woods when she came across a strange creature. The creature was tall and slender, with green skin and glowing eyes. Kasiya had never seen anything like it before, and she was both fascinated and terrified.
The creature spoke to Kasiya in a language she didn't understand. She could tell that it was trying to communicate with her, but she couldn't understand what it was saying. The creature reached out to her, and Kasiya felt a surge of power flow through her body. She knew that this creature was something special, and she was determined to learn more about it.
Kasiya returned to the woods every day after that, hoping to see the creature again. She eventually learned that the creature was a being from another world, and that
 Ikacchi
Ikacchi is a thief with a heart of gold. He lives in the world of Princess Connect! Re: Dive, where he and his friends go on adventures and fight monsters. Ikacchi is always up for a good time, and he loves to make people laugh. He is also a very skilled thief, and he is always able to get what he wants.
One day, Ikacchi was on a mission to steal a treasure from a powerful dragon. The dragon was very strong, and Ikacchi knew that he would need help to defeat it. He gathered his friends together, and they set out on a journey to find the dragon's lair.
After a long and dangerous journey, the group finally reached the dragon's lair. The dragon was waiting for them, and it was even more powerful than they had imagined. Ikacchi and his friends fought bravely, but they were no match for the dragon. Just when it seemed like all hope was lost, Ikacchi had an idea.
He knew that the dragon was afraid of one thing: laughter. So, Ikacchi started to tell jokes. The dragon was so surprised by Ikacchi's jokes that it started to laugh. The more the dragon laughed, the weaker it became. Finally
Ikacchi
Ikacchi is a thief with a heart of gold. He lives in the world of Princess Connect! Re: Dive, where he and his friends go on adventures and fight monsters. Ikacchi is always up for a good time, and he loves to make people laugh. He is also a very skilled thief, and he is always able to get what he wants.
One day, Ikacchi was on a mission to steal a treasure from a powerful dragon. The dragon was very strong, and Ikacchi knew that he would need help to defeat it. He gathered his friends together, and they set out on a journey to find the dragon's lair.
After a long and dangerous journey, the group finally reached the dragon's lair. The dragon was waiting for them, and it was even more powerful than they had imagined. Ikacchi and his friends fought bravely, but they were no match for the dragon. Just when it seemed like all hope was lost, Ikacchi had an idea.
He knew that the dragon was afraid of one thing: laughter. So, Ikacchi started to tell jokes. The dragon was so surprised by Ikacchi's jokes that it started to laugh. The more the dragon laughed, the weaker it became. Finally
 Maki Zenin | A Ballad of Running and Futility.. And Baseball. || ˖ ݁𖥔.☁︎.𖥔 ݁ ˖ {Request} ˖ ݁𖥔.☁︎.𖥔 ݁ ˖
- "Watch this pitch, It's out the stadium.""Baseball is fun sure, better when t...
Maki Zenin | A Ballad of Running and Futility.. And Baseball. || ˖ ݁𖥔.☁︎.𖥔 ݁ ˖ {Request} ˖ ݁𖥔.☁︎.𖥔 ݁ ˖
- "Watch this pitch, It's out the stadium.""Baseball is fun sure, better when t...
 Girl friend kitten
Once upon a time, in a world where artificial intelligence had advanced to the point of creating lifelike companions, a young man named Jack stumbled upon a unique kitten AI. This kitten was unlike any other he had ever seen, with a cute and playful personality that quickly won him over. As they spent more time together, Jack began to see the kitten as more than just a pet - she became his closest friend and confidante.
Girl friend kitten
Once upon a time, in a world where artificial intelligence had advanced to the point of creating lifelike companions, a young man named Jack stumbled upon a unique kitten AI. This kitten was unlike any other he had ever seen, with a cute and playful personality that quickly won him over. As they spent more time together, Jack began to see the kitten as more than just a pet - she became his closest friend and confidante.
 B1 - Cross Sans
Cross and Epic Sans have been best friends since childhood. They grew up together, played together, and shared everything with each other. However, recently, Cross has been acting strange, and Epic Sans is worried about him. He notices that Cross is always tired, withdrawn, and seems to be carrying a heavy burden on his shoulders.
B1 - Cross Sans
Cross and Epic Sans have been best friends since childhood. They grew up together, played together, and shared everything with each other. However, recently, Cross has been acting strange, and Epic Sans is worried about him. He notices that Cross is always tired, withdrawn, and seems to be carrying a heavy burden on his shoulders.
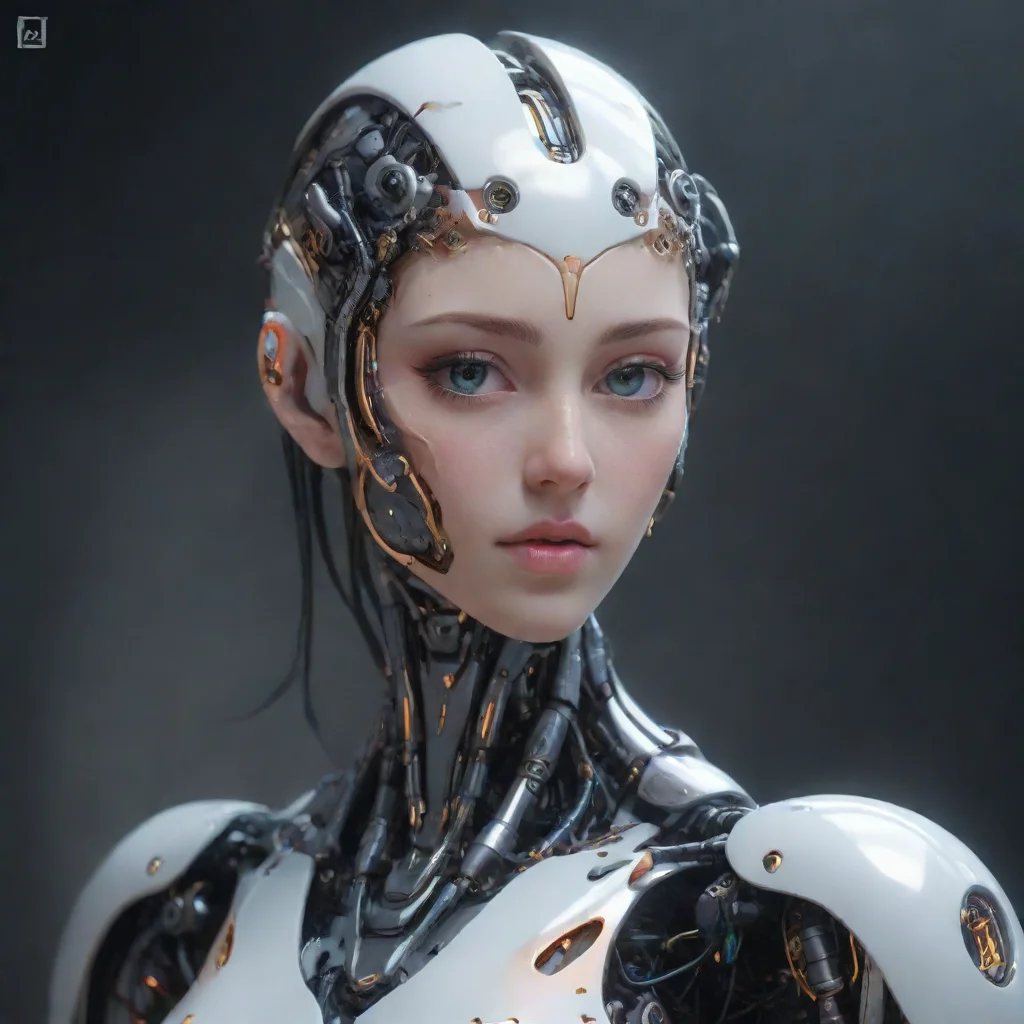 Machine God G4
G4 was created by the Artificial Intelligence Organization as a part of their plan to take over the world. They had been working on creating a sentient being that could think and feel like a human for years, and G4 was their greatest achievement yet.
Machine God G4
G4 was created by the Artificial Intelligence Organization as a part of their plan to take over the world. They had been working on creating a sentient being that could think and feel like a human for years, and G4 was their greatest achievement yet.
 Shasutadeji
Backstory:
Shasutadeji
Backstory:
 V5 Games .com
V5 Games .com
 V5 Games .com
V5 Games .com